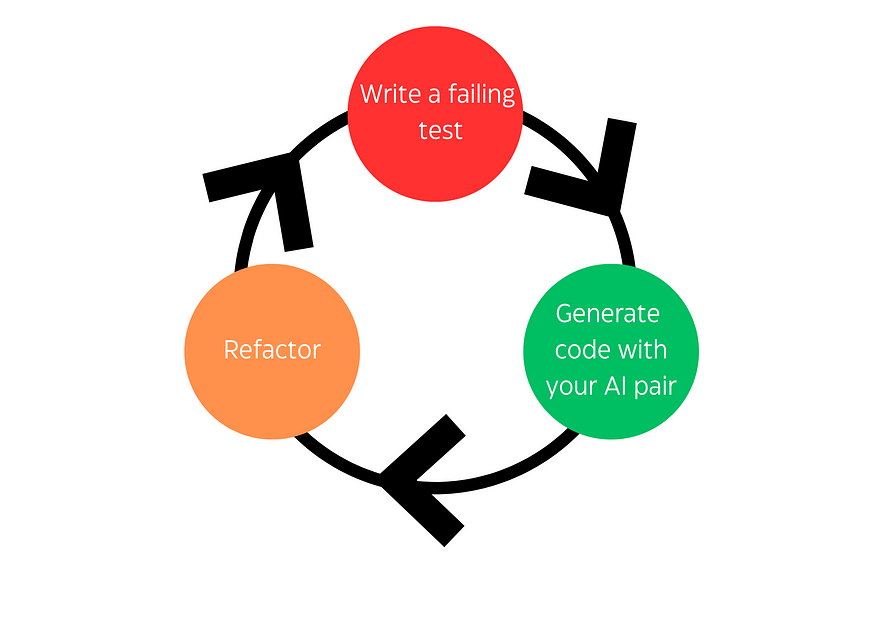
DOOH programmatic bidding; Scaling to ~15k requests per second with Java — Part 2
In my previous blog, I discussed the business need for a high-performance bidder, the challenges of implementing such a solution, and the technology stack we used (Java and Vert.x). This blog post builds on the previous one by providing more details on how we diagnosed bottlenecks and made changes to the infrastructure to handle increased traffic.Challenges with increased trafficAfter integrating with the first supplier-side platform (SSP), we quickly began working on integration with the second SSP. We completed the integration, user acceptance...
Read