In a data pipeline architecture, it is often challenging to efficiently read a batch of messages from Kafka and write them to AWS S3 while reducing storage costs. To achieve this, Apache Flume was employed, an effective tool for collecting and moving large amounts of log data in real-time.
This use case revolves around reading messages from Kafka in bulk, and then buffering them temporarily before transferring them to S3 in larger batches. This batching mechanism helps reduce API calls to S3, thereby lowering costs. However, during implementation, a significant bottleneck was encountered that slowed down the system – the startup time for Flume agent pods in our Kubernetes environment. This issue, caused by extensive permission checks during pod initialization, hindered the ability to scale the system efficiently. Addressing this bottleneck is quite important.
As part of the scalable data ingestion system, a Persistent Volume Claim (PVC) was introduced as a buffer. This PVC temporarily stored incoming Kafka messages before transferring them to AWS S3 under specific conditions. While this approach helped reduce the number of write operations to S3, introducing PVCs brought new performance challenges, particularly related to pod startup times.
When deploying Flume agents, significant delays were noticed during pod initialization, particularly in scenarios involving persistent storage and security context handling. Kubernetes, by default, performs strict permission checks on volumes to ensure compliance with the pod’s security policies. While these checks are essential for maintaining a secure environment, they introduce considerable overhead, slowing deployments and reducing system responsiveness during peak load periods.
To mitigate this performance hit, several optimization techniques were introduced with one of the most promising being Kubernetes’ fsGroupChangePolicy configuration. By adjusting this policy, control was gained over how Kubernetes handles the file system group ownership changes for volumes during pod initialization. Rather than enforcing these changes every time a pod starts, fsGroupChangePolicy the process can be streamlined by reducing unnecessary permission checks while maintaining security. This blog post details the journey of implementing this strategy, which significantly improved Flume agent pod startup time and optimized the data pipeline for both speed and cost efficiency.
Understanding Security Context in Kubernetes 🔐
Imagine a gated apartment complex (the Pod) with individual units (Containers). The security context is like the building’s security system 👮♂️. It defines who can enter (user ID), which groups they belong to (group ID), and what actions they can take (capabilities). One key element is the “tenant group” (fsGroup), which determines access privileges to common areas like the pool or gym (files and directories).
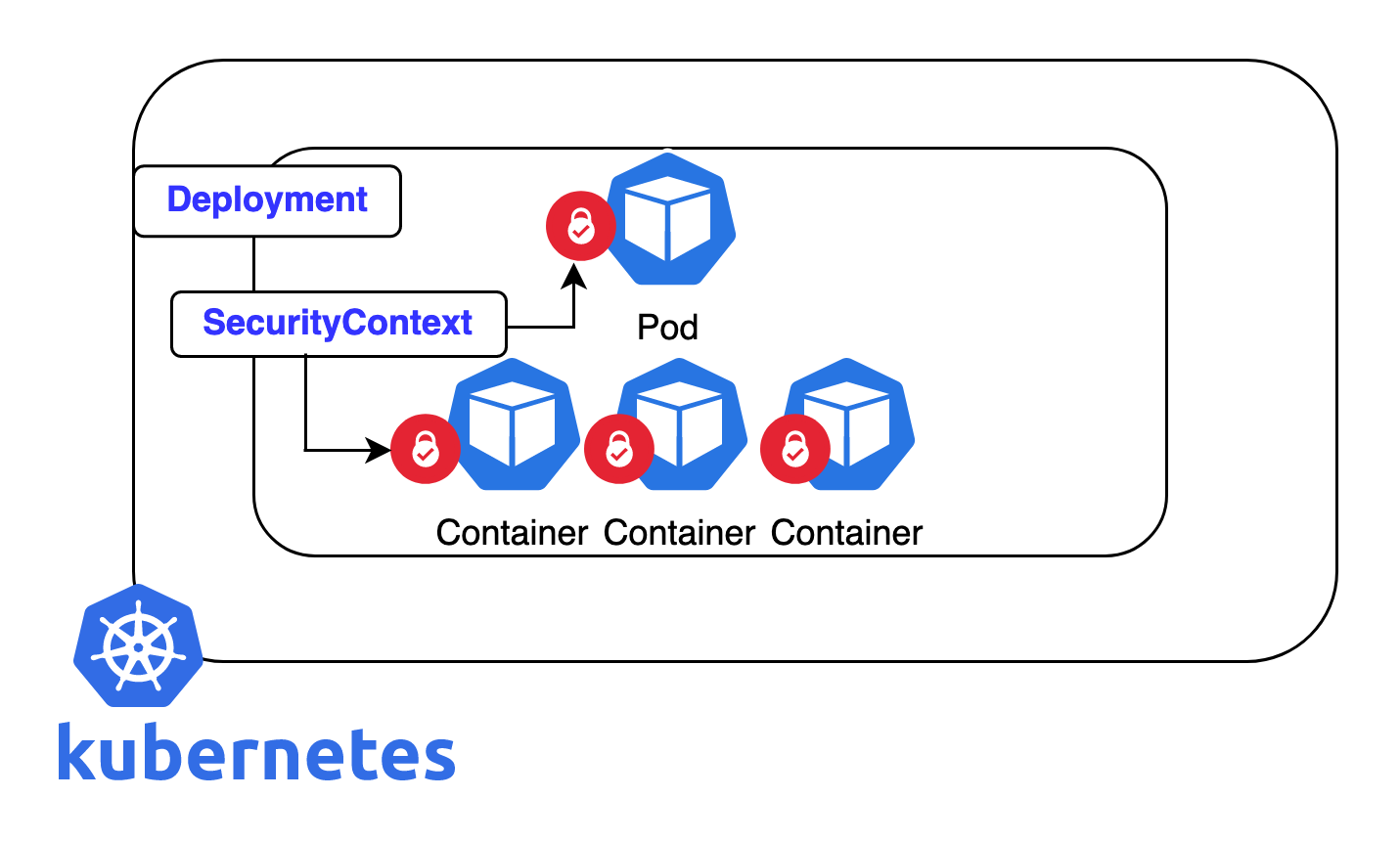
Understanding Security Context in Kubernetes: Access Control for Your Pods
Kubernetes (often abbreviated as k8s) is an open-source system for automating deployment, scaling, and management of containerized applications. It groups containerized applications into logical units called Pods and manages them across a cluster of machines.
Security context 🔑 is a fundamental concept in Kubernetes that defines the access control settings for pods. It dictates three main aspects:
User ID (UID): Similar to a user account on a traditional operating system, the UID identifies the user or process running within the container. This helps ensure that only authorized processes can execute within the pod.
Group ID (GID) and fsGroup: While a UID specifies the individual user, the GID defines the group a process belongs to. This group membership is crucial for controlling access to resources within the pod. In Kubernetes, a specific group ID used for access control within a Pod is often referred to as the “tenant group” (fsGroup). It determines the level of access processes have to share resources like files and directories mounted into the container.
Capabilities: Capabilities are a set of privileges that grant processes within the container-specific actions beyond basic file system operations. For example, a process might require network access (CAP_NET_ADMIN) or the ability to mount devices (CAP_SYS_MOUNT). Security context allows you to define a limited set of capabilities for the processes running in the container, enhancing security by restricting unnecessary privileges.
In essence, the security context acts as a security layer for your Pods. It ensures that only authorized processes with the appropriate user ID, group membership (fsGroup), and capabilities can execute and interact with resources within the Pod.

The Challenge: Sluggish Startup Times ✖️
Issue: Assigning a specific tenant group can be necessary for certain applications, but it can also introduce delays during pod startup. 🪫
Traditional Approach: Kubernetes acts like a security guard, checking every unit (file/directory) within the mounted volumes (shared storage) to ensure they comply with the assigned group permissions. This process can be lengthy, particularly for large storage units.
Impact: These checks can become a bottleneck in scenarios where speed is critical.
Factors Influencing Pod Startup Time
Image size: Larger images require more time to download.
Number of containers: A higher number of containers leads to longer startup times.
Volume mounts: Mounting volumes can be time-consuming.
Network latency: Delays in network communication can impact startup time.
Application complexity: Complex applications with extensive initialization logic might take longer.
Kubernetes cluster load: High resource utilization can slow down pod creation.
The Solution: fsGroupChangePolicy to the Rescue 😎
Kubernetes introduced fsGroupChangePolicy to address this performance challenge. This setting allows you to fine-tune how Kubernetes handles volume permission checks for pods with a defined tenant group.
Options:
OnRootMismatch (Recommended): Focuses permission checks only on the mounted storage unit’s main entrance (root directory). If the ownership or permissions there differ from the expected values, Kubernetes performs the necessary modifications. This significantly reduces the number of files checked and potentially modified, leading to faster startup times.
File: Enforces permission checks on every unit within the storage unit, regardless of its type or access mode. While it offers the most granular control, it can lead to slower startup times for large volumes.
None: Disables permission checks altogether. Use it cautiously, as it relies entirely on pre-configured volume permissions, which could introduce security vulnerabilities.
Accelerating Pod Startup: Optimizing StatefulSet with fsGroupChangePolicy
Why Optimization Was Essential
Whenever the StatefulSet (STS) pods underwent a rollover, the meticulous process of resetting and re-assigning mount permissions to the newly created pod proved to be an extraordinarily time-consuming challenge. This was primarily due to the complexities in managing fsGroup changes, which often extended the process to several hours. While removing fsGroup altogether appeared to be a viable solution as it was non-essential for this specific use case, it was soon realized that this approach compromised the necessary permissions for the main user to execute intended operations.
It became evident that a solution was required to preserve essential permissions without compromising the underlying permission policy. This is where the fsGroupChangePolicy configuration was introduced.
Before Optimization
securityContext:
fsGroup: 1004Updated Configuration (Optimized Startup):
securityContext:
fsGroup: 1004
fsGroupChangePolicy: "OnRootMismatch" # Optimizes permission checksBefore optimization: 1 min 20 seconds (as you mentioned)
After optimization (with
fsGroupChangePolicy: OnRootMismatch): 30-35 seconds
Pod startup times were measurably reduced, leading to faster deployments and improved overall performance.
Conclusion
Optimizing pod startup time is paramount for ensuring efficient and scalable Kubernetes environments, especially when managing a substantial number of services like a system with approximately 50 services. By leveraging, fsGroupChangePolicy: "OnRootMismatch" a valuable balance between security 🔐 and performance ⏰ can be achieved in Kubernetes deployments. Consider the application requirements carefully and choose the appropriate security context settings. This optimization technique can streamline the deployments and ensure the applications are running faster than ever.
References:



